If you’re like most registrar leaders, transcript fraud keeps you up at night more than it should.
Through our partnerships with university registrar teams across North America and Europe, we’ve watched firsthand as academic credential fraud has evolved from simple document alterations to sophisticated criminal enterprises. The numbers tell the story: the global academic fraud industry is now worth an estimated 21 billion dollars annually, and traditional verification methods simply can’t keep pace.
But here’s the good news—this comprehensive guide will walk you through a sequenced, practical roadmap that you can implement step-by-step, combining proven strategies with modern technology to reduce fraud risks while actually making your team’s life easier.
Let’s explore the 7 essential steps that will help you stop transcript fraud before it touches your institution’s reputation.
The Risk of Academic Transcript Forgery
Let’s be honest—fake transcripts have become a serious business problem.

We’re not talking about students making amateur alterations in their dorm rooms anymore. Professional forgery operations now produce documents that would make even your most experienced staff do a double-take.
Here’s what caught my attention: criminal enterprises have made credential fraud so sophisticated that 4.7 billion people globally have either acquired or been affected by fake degrees.
These operations invest in the same professional-grade equipment your institution uses. They’ve got your letterheads, they understand your formatting, and frankly, they’re getting really good at what they do.
The challenge? Today’s forgeries require specialized knowledge to detect. Where you used to spot fakes through obvious formatting errors or poor print quality, now you need systematic verification processes just to tell the difference.
Institutional Risks Run Deeper Than Most Registrars Realize
Financial aid fraud alone has surged to over $100 million per year as of 2023, compared to less than $10 million annually before 2020.
This dramatic increase demonstrates how quickly fraud techniques evolve and the escalating costs institutions face from inadequate security measures. As a result of such instances we see that :-
-
Accreditation bodies scrutinize institutions with credential integrity issues more closely: The Middle States Commission on Higher Education and other regional accreditors now include credential security as part of their evaluation criteria. Poor transcript security can trigger additional compliance requirements.
-
Federal compliance violations multiply when transcript fraud goes undetected: FERPA requires institutions to maintain accurate educational records. When fraudulent transcripts enter the system, universities may face Department of Education investigations and potential funding withdrawal, which represents the most severe penalty available under federal education law.
-
Rankings and partnerships suffer as credential fraud becomes public: International university partnerships often dissolve when credential integrity comes into question. U.S. News & World Report and similar ranking organizations factor institutional reputation into their methodologies.
The Human Cost Involved
Here’s why this work matters beyond institutional concerns.
When unqualified people slip through with fake credentials in healthcare, engineering, or education, real people get hurt. The National Association of Credential Evaluation Services has documented patient safety incidents linked to fraudulent medical credentials across multiple states.
Universities that continue experiencing high-profile data breaches face million-dollar remediation costs and intensive compliance investigations. The courts are increasingly holding universities accountable when lax verification processes enable fraud that harms others.
But here’s the encouraging news: you can prevent most of this. The solution isn’t about finding one magic fix. It’s about building layered defenses that make fraud exponentially more difficult and expensive for criminals.
When you combine better processes with modern technology and enhanced staff awareness, you create barriers that most fraud operations simply can’t overcome.
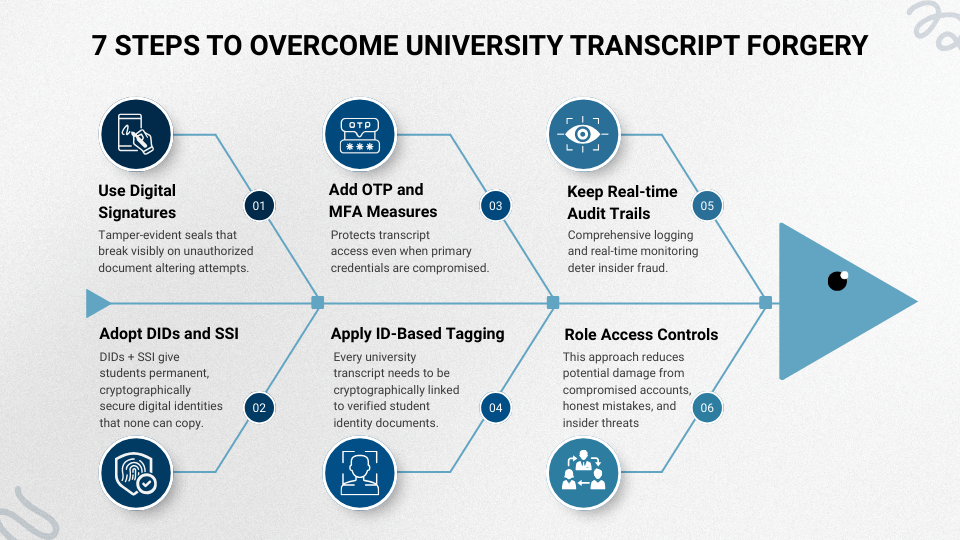
Step 1: Use Digital Signatures on Every Transcript
Let me start with the security measure that gives you the biggest impact for your effort.
Digital signatures provide the strongest defense against transcript alteration and forgery. Think of them as tamper-evident seals that break visibly when anyone tries to modify your document.
Here’s what makes them special: unlike physical seals or watermarks, digital signatures use mathematical algorithms that make forgery technically impossible with current technology.
When your office digitally signs a transcript, the system creates a mathematical fingerprint of the entire document. This fingerprint gets encrypted with your institution’s private key, creating the digital signature that travels with the document.
Why Your Current Approach Isn’t Working
I know you’ve probably invested in security paper and official seals—most registrar offices have.
But here’s the reality: once someone scans that beautiful, secure paper transcript into a PDF, all your physical security features become meaningless. Forgers simply edit the scanned image and print new copies on similar paper stock.
Those traditional security features that cost you money? Professional forgers have databases of university letterheads, seals, and formatting templates.
They often buy security paper from the same suppliers you use. The investment you’ve made in physical security is working against criminals who were amateurs five years ago—but today’s operations are far more sophisticated.
And I’m betting your staff spends way too much time on verification calls.
Our analysis of registrar workload data shows that verification calls consume an average of 47 minutes per staff member daily. During peak hiring seasons like September through November, these calls can completely overwhelm your office operations.
How Digital Signatures Change Everything
Here’s what I find most impressive about digital signatures: they protect every single element of your transcript.
Unlike physical seals that only cover one area, digital signatures create mathematical protection for every character, image, and formatting element. Change even one grade or credit hour, and the signature breaks instantly.
When someone receives your digitally signed transcript, they get immediate confirmation it came from your institution. The verification shows your institution name, the signing date, and the certificate authority that issued your signing credentials. This creates an unbreakable chain of authenticity that criminals simply can’t replicate.
And when fraudsters try to alter a signed transcript? The warning messages are unmistakable. Red warning icons are displayed with text like “Document has been altered since it was signed.” These warnings make altered documents completely unusable for legitimate purposes.
Making Verification Simple for Everyone
Now, let’s talk about making this work for the people who actually need to verify your transcripts.
I recommend creating a dedicated transcript verification portal where employers can check authenticity instantly. Think of it as a simple web form that accepts document hashes or verification codes and works 24/7—no more interrupting your staff during the workday.
Here’s a small change that makes a huge difference: include verification instructions directly on every transcript. Add a footer with something like: “Verify this transcript’s authenticity at [university].edu/verify or call the Registrar’s Office at XXX-XXX-XXXX.” Clear instructions prevent confusion and those misdirected calls we all hate.
And please, make sure your verification process shows up when employers Google it.
Employers often search “[University name] transcript verification” when they receive documents. If your verification process appears prominently in search results, you’ll save everyone time.
One more tip I always share: track your verification metrics. Monitor how many employers use your portal versus calling your office. These numbers help justify technology investments to administration and demonstrate real ROI when budget time comes around.
| Feature | Paper Transcripts | Digitally Signed Transcripts |
|---|---|---|
| Verification Method | Phone calls to registrar | Instant digital verification |
| Tamper Resistance | Easily altered when scanned | Mathematically impossible to alter |
| Turnaround Time | 2-5 business days | Immediate upon signing |
| Verification Effort | 5-15 minutes per transcript | 10-30 seconds automated |
| Security Features | Physical seals, watermarks | Cryptographic signatures |
| Cost per Transcript | $3-7 (printing, mailing) | $0.10-0.50 (digital processing) |
| Storage Requirements | Physical filing systems | Digital archives with backup |
| Environmental Impact | Paper, ink, shipping | Minimal digital footprint |
Comparison: Paper vs. Digitally Signed Transcripts
Step 2: Adopt Decentralized Identifiers and Self-Sovereign Identity
I’ll be honest—this next step sounds more complicated than it actually is.
Decentralized identifiers (DIDs) give students permanent, cryptographically secure digital identities that no one else can impersonate. Think of it this way: instead of just protecting the transcript document itself, we’re creating unforgeable student identities that connect directly to their academic records.
The technology builds on World Wide Web Consortium (W3C) standards, which means it’s not some experimental approach.
These verifiable credentials represent academic achievements as digitally signed data structures with three essential parts: your institution’s signature, the student’s identity binding, and clear issuance/expiration information.
Why does this matter for your daily operations? It makes fraud exponentially more expensive for criminals.
Instead of just forging a document, criminals would need to create fake student identities, somehow compromise your signing keys, and manipulate distributed systems. Most fraud operations simply can’t handle that level of complexity.
What This Actually Means for Your Students
Let’s break this down in practical terms.
Each student gets a unique digital identifier that belongs exclusively to them—think of it like a permanent, secure social security number for academic records. Students control this identifier throughout their educational journey and career.
Here’s where it gets interesting: academic credentials link directly to this identifier through cryptographic binding.
When you issue a transcript, it gets mathematically tied to the student’s DID. Only that specific student can present these credentials for verification—nobody else can use them, even if they somehow get access to the documents.
And students actually gain more control over their records, not less. Unlike traditional transcripts that students can’t control after you issue them, DID-based credentials let students selectively share specific courses, degrees, or GPA information based on what employers actually need.
For transfer students, this is particularly elegant. Their DID stays constant even when they move between institutions. All their academic records from different universities can link to the same verified identity, creating a complete and trustworthy academic history.
The Security That Actually Works
Here’s what I love about this approach: transcripts issued with DIDs get recorded in distributed, tamper-resistant systems.
Instead of relying on a single database that hackers could potentially compromise, DID systems spread record-keeping across multiple nodes. Altering records would require compromising most of the network simultaneously—which is practically impossible.
Remember those employer verification calls I mentioned earlier? This eliminates most of them. Verification happens through automated cryptographic processes rather than manual phone calls or email exchanges. The system automatically checks both the student’s identity and your institutional signature.
You also get permanent audit trails that track all credential interactions.
Every time someone issues, shares, or verifies a credential, the system records these actions with timestamps and digital signatures. This creates forensic evidence that can identify fraud attempts before they cause damage.
And here’s a security benefit you might not expect: even if hackers breach your student information system, they still can’t forge DID-based credentials. That’s because students’ private keys are stored separately from your institutional systems. Criminals would need to compromise multiple independent systems to create convincing fakes.
What This Means for Your Institution
The bottom line? Forgeries become nearly impossible because the system validates both student identity and your institutional authorization.
Criminals would need to compromise multiple independent systems to create convincing fakes. The technical complexity and cost make fraud economically unfeasible for most operations.
You retain full authority over what credentials you issue and when. Students control the sharing and presentation, but they can’t modify the underlying academic data you’ve certified.
International recognition gets much easier too. Global employers and universities can verify your graduates’ credentials using the same technical standards, reducing friction in international hiring and admissions processes.
And compliance with data protection regulations becomes simpler. GDPR, FERPA and similar privacy laws require student consent for data sharing. DID systems build consent management directly into the credential sharing process, so you’re covered automatically.
Step 3: Add OTP and Multi-Factor Authentication
One-time passwords (OTP) and multi-factor authentication create additional security layers that protect transcript access even when primary credentials are compromised.
These technologies work on a simple principle: requiring multiple forms of verification makes unauthorized access exponentially more difficult. Even if someone steals a password, they still need access to the second authentication factor.
The implementation must balance security improvements with user experience to ensure adoption.Overly complex authentication systems frustrate legitimate users and often get bypassed through workarounds.
Effective MFA feels seamless to authorized users while creating insurmountable barriers for attackers.
OTP for External Access
Require one-time passwords whenever external parties request transcript access.
When employers click transcript verification links, the system should send OTP codes to the student’s registered email or phone number. This ensures students know when their records are being accessed.
Students should receive immediate notifications and can approve or deny access requests. Notification messages should include who is requesting access, what specific records they want to see, and how long the access will remain valid. Students can then make informed decisions about sharing their information.
This prevents unauthorized viewing when transcript links get shared accidentally. Email forwards, copied URLs, and other unintentional sharing become harmless when each access requires fresh OTP verification. Only the legitimate student can authorize viewing.
Time-limited access also reduces the window for fraudulent use. OTP codes should expire within 15-30 minutes of generation. This narrow window prevents criminals from using stolen codes hours or days after intercepting them. The system further creates detailed logs of all access attempts for audit purposes too.
Every OTP generation, successful authentication, and failed attempt should be recorded with timestamps, IP addresses, and user agent information. These logs help identify suspicious patterns, if any.
MFA for Registrar Staff
Let’s talk about protecting your registrar staff accounts—because honestly, passwords alone just aren’t enough anymore.
When staff use weak passwords, reuse the same credentials across multiple systems, or click that one convincing phishing email, single-factor authentication completely fails. However, adding just one more authentication step prevents most unauthorized access attempts.
For most of your team, text message codes work perfectly and are simple to set up. SMS-based authentication works with any mobile phone, doesn’t require downloading special apps, and lets staff authenticate from anywhere. They get their codes instantly and can log in whether they’re in the office or working from home.
Now, for staff who handle your most sensitive records, I’d recommend stepping up to authentication apps. Google Authenticator, Microsoft Authenticator, and similar apps generate time-based codes that work even without cell service. Plus, these apps are much harder for criminals to compromise through SIM-swapping attacks than regular text messages.
Your administrators who can modify grades or access multiple student accounts? They need the strongest protection available. Physical security keys like YubiKey devices provide maximum security because they resist both phishing attempts and malware that might compromise software-based authentication.
And please don’t forget about emergency situations. What happens when someone’s phone dies right before they need to process urgent transcripts?
Make sure you have secure backup methods in place—like pre-generated backup codes stored in your office safe—so staff can regain access without compromising security.
Step 4: Apply ID-Based Tagging to All Transcripts
Here’s where we get into preventing one of the most common types of transcript fraud: students using each other’s legitimate records.
Every university transcript needs to be cryptographically linked to verified student identity documents. This creates an unbreakable connection between academic records and the specific person who actually earned them—which sounds complex, but it’s actually quite straightforward to implement.
The key is systematic collection and verification of primary identity documents right from enrollment. You need clear policies about which identity documents you’ll accept and exactly how you’ll verify their authenticity. When practices are inconsistent across your team, you create vulnerabilities that criminals love to exploit.

Link Transcripts to the Right Student
Rather than storing complete identity document images, which creates privacy risks, it is better to create secure cryptographic hashes of key identity information.
Think passport numbers, social security numbers, driver’s license numbers, and student ID numbers. These hashes confirm identity without exposing sensitive personal data that could be misused if your system gets breached.
Make it a point to use multiple identity markers as single documents can be forged or stolen. When you use several markers together—like passport plus SSN plus biometric data—impersonation becomes exponentially more difficult and expensive for criminals.
International students need special consideration since they present different combinations of identity documents. Students from various countries might have passports, national ID cards, educational certificates, or other documents. Your system needs to accommodate these differences while maintaining consistent security standards across all student populations.
Don’t forget about students who change their identity information during their academic careers. Name changes, citizenship updates, and other identity shifts happen regularly. Plan for periodic reverification to ensure your transcript tagging stays accurate and current throughout each student’s journey.
Automate the Checking Process
The beauty of modern systems is that they can cross-reference transcript identity tags with your current student records automatically—before any transcript gets issued.
This automated verification prevents human error and ensures your identity checking policies get applied consistently every single time, without adding extra work for your staff.
When identity verification fails, the system should immediately freeze transcript processing and alert your senior staff. These alerts need to include specific details about exactly what information didn’t match, so your team can investigate quickly and efficiently.
Machine learning algorithms can help you spot suspicious patterns that might slip past manual review.
For example, multiple transcript requests for the same student coming from different IP addresses, or requests that happen right after identity document changes. These patterns often indicate fraud attempts that human reviewers might miss. I always recommend regular audits to verify your identity tagging stays accurate over time.
Monthly or quarterly reviews of a random transcript sample help catch system errors or potential fraud. When you find discrepancies, they might indicate technical problems that need fixing or actual fraud attempts that require investigation.
Integration with national identity verification services provides additional confirmation. Services like E-Verify or similar identity verification platforms can confirm that student-provided identity information matches government databases.
Step 5: Keep Audit Trails and Monitor in Real Time
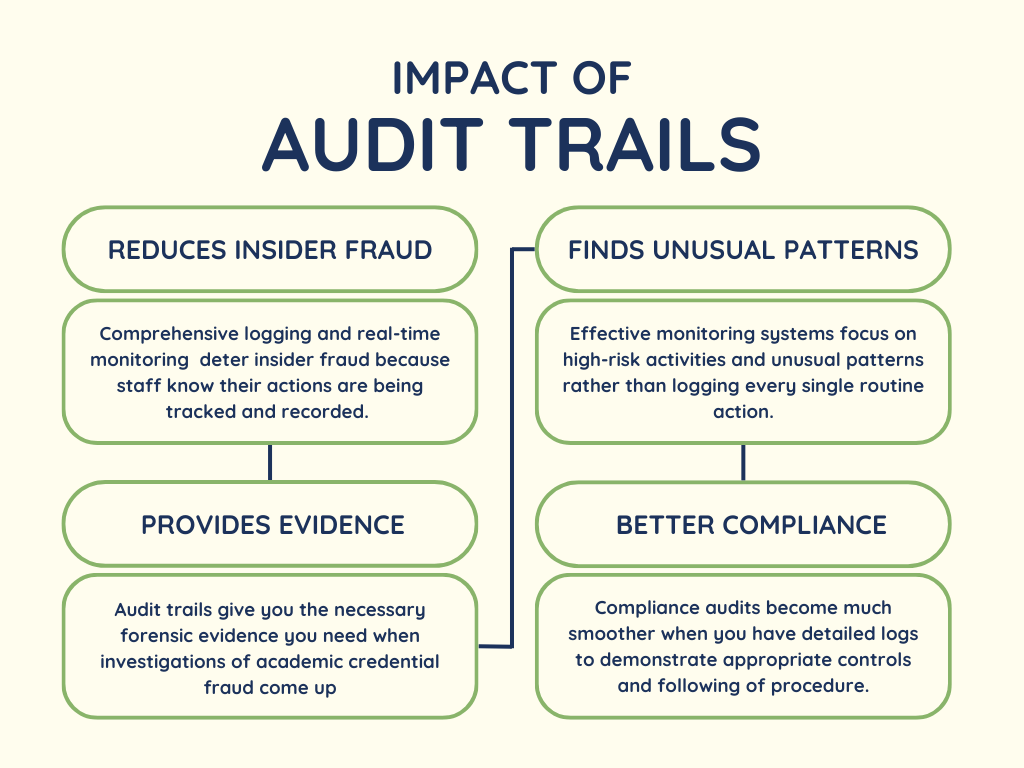
Comprehensive logging and real-time monitoring serve two crucial purposes in your fraud prevention strategy.
First, they deter insider fraud because staff know their actions are being tracked and recorded. Second, they give you the forensic evidence you need when investigations become necessary—and trust me, having detailed logs makes those conversations with administration much easier.
The secret is capturing the right information without drowning your team in false alerts.
Effective monitoring systems focus on high-risk activities and unusual patterns rather than logging every single routine action. This targeted approach keeps alert volumes manageable while maintaining comprehensive oversight of your most sensitive operations.
Record Every Action
Every single transcript interaction should generate detailed log entries that create a complete chain of custody for your academic records.
I’m talking about capturing staff member identity, which student record was accessed, what specific actions were taken, and exact timestamps. This level of detail might seem excessive, but it’s invaluable when you need to trace what happened during a security incident. Here’s something crucial: your audit logs need to be tamper-resistant to maintain their forensic value.
If audit logs are stored in the same system as your student records, users with administrative access could potentially alter them. Separate logging systems with write-only access prevent unauthorized modifications that could cover up fraudulent activities.
Don’t forget to capture automated processes alongside manual user activities. Things like batch transcript generation, scheduled reports, or system maintenance should also generate audit entries.
This gives you complete visibility into all record access, whether it’s human-initiated or system-driven, so you never have gaps in your security monitoring.
Including contextual information helps you distinguish between normal activity and potential problems. Log entries should show whether access happened during business hours, from recognized IP addresses, and as part of routine workflows. This context makes it much easier to spot genuinely suspicious behavior among all the normal daily activities.
Detect Suspicious Activity
Smart automated alerts can catch potential problems before they turn into major security incidents.
Set up monitoring for multiple transcript downloads within short timeframes—legitimate users rarely need more than one or two transcripts per student in a single day, so rapid-fire downloads often signal data theft attempts or unauthorized bulk access.
Pay attention to access attempts during unusual hours or from unexpected locations. When staff access student records at 2 AM or from foreign IP addresses, that’s worth investigating.
Geographic monitoring can flag access attempts from unexpected countries or regions that don’t match your staff’s normal work patterns.
Track repeated failed login attempts that might indicate someone’s trying to break in. Multiple failed passwords for the same account suggest automated attack tools attempting to guess credentials. Progressive lockout policies should kick in after three to five failed attempts, and you should get alerts about these patterns.
Look for unusual patterns in record modification requests too. Grade changes or transcript corrections that cluster around specific time periods might indicate coordinated fraud attempts, while unusual approval patterns could reveal compromised administrator accounts.
Consider enhanced monitoring for high-profile student records. Celebrity children, government officials, or students in security-sensitive programs often become targets for social engineering attacks. Extra vigilance for these records can prevent privacy breaches that make headlines.
Why It Matters
The psychological impact of comprehensive logging cannot be overstated—when staff know their actions are permanently recorded and regularly reviewed, it deters most opportunistic fraud attempts.
FERPA compliance audits become much smoother when you have detailed logs to demonstrate appropriate controls. Auditors want to see evidence that you’re following policies and detecting violations when they occur.
When suspicious activity does get detected, detailed logs enable rapid incident response. Investigators can quickly understand the scope of unauthorized access, identify which records might be affected, and determine whether other accounts could be compromised.
Plus, you get valuable operational insights from analyzing access patterns over time. Log analysis can reveal workflow bottlenecks, identify training needs, and highlight opportunities to improve system usability. This operational intelligence helps justify technology investments and makes the case for appropriate staffing levels to administration.
Step 6: Strengthen Access Controls for Staff
Let’s address one of the most common causes of transcript fraud within institutions: overprivileged accounts and inconsistent permission management.
Role-based access controls ensure your staff members can only perform actions that match their actual job responsibilities and experience level.
Too many security incidents are caused by junior staff having access to sensitive functions, shared passwords creating accountability gaps, and permissions that never get updated when people change roles.
All these security incidents lead to the increase of insider threat for an organization.
The principle that should guide every access decision is simple: users get the minimum permissions necessary to do their job effectively. This approach reduces potential damage from compromised accounts, honest mistakes, and insider threats, while regular access reviews ensure permissions stay appropriate as job roles naturally evolve over time.
Role-Based Permissions
Here’s a practical approach: limit transcript issuance authority to your most experienced and reliable senior staff members.
Junior employees and temporary workers simply shouldn’t have direct transcript issuance capabilities. These permissions should require several years of demonstrated reliability and thorough background verification—it’s not about trust, it’s about reducing risk exposure.
Grade editing represents one of your highest-risk activities, so restrict those capabilities to specifically authorized personnel only. These modifications should require special approval workflows and additional training.
Consider implementing hierarchical approval requirements based on the sensitivity of different operations. Simple address updates might only need staff-level approval, while grade changes require supervisor sign-off, and bulk transcript processing needs department head authorization.
It is always recommended creating separate administrative accounts for privileged operations.
Staff should have two accounts: their standard daily-use account with limited permissions for routine work, and an administrative account reserved for sensitive operations. This separation dramatically reduces the impact if their regular account gets compromised during normal activities.
Manage Accounts Securely
Strong password policies need to balance security requirements with practical usability—overly complex requirements often backfire. Passwords should be at least 12 characters with mixed case letters, numbers, and symbols, but don’t make them so complicated that staff start writing them down or using predictable patterns. The goal is security that people can actually follow consistently.
Multi-factor authentication should be mandatory for every single staff member who accesses student records, regardless of their role or seniority level. This requirement needs to apply to both on-campus access and remote work situations.
Account deactivation when staff leave must happen within hours of their final workday, not days or weeks later. Departure procedures should include immediate account deactivation as a standard checklist item. Delayed access removal creates unnecessary windows for potential misuse by terminated employees who might feel disgruntled.
Quarterly access reviews should be non-negotiable for maintaining security over time. These audits need to verify that each staff member’s current permissions actually match their job responsibilities. People who change roles often keep old permissions that are no longer appropriate, creating unnecessary security risks.
Add Dual Approvals
Two-person authorization for grade corrections and transcript modifications is essential—and the person requesting the change must be different from the person approving it.
This separation prevents any single individual from making unauthorized modifications that could slip through unnoticed. It’s a simple check that catches both honest mistakes and intentional fraud attempts.
Digital approval workflows that create permanent audit trails are far superior to email approvals or verbal authorizations. Digital systems capture both approvals with precise timestamps and digital signatures, giving you the documentation you need for compliance audits and fraud investigations. Email threads and verbal confirmations just don’t provide adequate proof.
When the first approver rejects a change request, you need clear escalation procedures to prevent approval shopping. Staff shouldn’t be able to keep asking different supervisors until someone says yes. Established procedures should govern how to appeal rejected requests and obtain legitimate secondary reviews when circumstances warrant them.
Emergency procedures for urgent changes outside normal business hours require special planning. Student emergencies sometimes demand immediate transcript modifications, but you can’t abandon security for convenience. Pre-approved emergency procedures should enable rapid response while maintaining dual approval requirements through designated on-call staff members.
Step 7: Train Staff and Build a Security Culture
Here’s the truth: technology is only as strong as the people using it. Comprehensive staff training creates that crucial human firewall that complements all your technical security measures.
Your team members need to understand fraud techniques, follow consistent security procedures, and serve as that final line of defense against sophisticated attacks that might slip past automated systems.
Effective training goes way beyond those one-time security sessions that everyone forgets about after a week. You need ongoing security awareness that gets reinforced through real-world examples and stays current with evolving threats.
Staff need to understand not just what procedures to follow, but why these steps matter for protecting your institution’s reputation and your students’ futures.
Teach Staff to Recognize Forgeries
Your team needs practical training to identify red flags in both physical and digital transcript submissions they encounter daily.
Common forgery indicators include inconsistent formatting, incorrect institutional terminology, missing security features, and unusual request patterns. Staff should develop familiarity with what authentic transcripts from peer institutions actually look like in normal circumstances.
Real-world forgery examples from law enforcement and industry reports provide the most effective learning experiences. These concrete examples stick in people’s minds much better than theoretical discussions about what fraud might look like. Law enforcement partners often share anonymized fraud samples specifically for training purposes—take advantage of these resources.
Role-playing exercises help staff apply their knowledge under realistic pressure. Practice scenarios where team members evaluate suspicious transcript requests build both confidence and decision-making skills. These simulations should include both obvious fraud indicators and subtle red flags that require more careful analysis.
Regular updates about evolving fraud techniques are absolutely essential because criminal methods change rapidly. Monthly security briefings should cover recent fraud trends, new detection methods, and lessons learned from other institutions. What worked to catch fraud last year might not work against this year’s techniques.
Standardize Verification Procedures
Clear, step-by-step protocols for verifying incoming transcripts from other institutions eliminate the guesswork that creates vulnerabilities.
Written procedures ensure consistency across different staff members and reduce the temptation to take shortcuts that compromise security. These protocols should specify exactly what verification steps are required and what documentation needs to be maintained.
Convenience shortcuts like accepting transcripts sent to personal email addresses are exactly how fraudsters bypass your security.
Criminals specifically try to circumvent institutional verification by requesting documents be sent to personal accounts that don’t have proper security controls. All transcript communications must flow through your official institutional email systems without exception.
Verification checklists that staff can follow systematically reduce human error and ensure completeness. Digital checklists can integrate directly with your student information system to track completion of required steps. This systematic approach prevents staff from accidentally skipping crucial verification elements during busy periods.
Clear escalation procedures prevent delays when verification raises red flags. Staff should know exactly who to contact and how quickly to act when they suspect fraudulent documents. Unclear escalation procedures lead to hesitation and delayed responses that can allow fraud attempts to succeed.
Build a Culture of Security
Creating an environment where staff feel comfortable reporting suspicious requests without fear of criticism is absolutely crucial.
When security concerns get dismissed or criticized, people stop raising them. Staff should feel confident that questioning unusual requests is valued and appreciated, not seen as being difficult or slowing things down.
Regular communication about new fraud methods and industry trends keeps security awareness sharp. Security newsletters, brief team meeting updates, and email alerts help maintain high awareness levels. Staff who understand current threats are naturally better prepared to recognize and respond to them when they encounter suspicious situations.
Close coordination with IT security and admissions teams ensures consistent approaches across your institution. Regular coordination meetings prevent contradictory policies and ensure everyone’s working toward the same security goals.
Recognizing and rewarding staff who identify potential fraud attempts encourages continued vigilance. Positive reinforcement for security-conscious behavior motivates ongoing attention to security details. Simple recognition in team meetings or newsletters can be surprisingly effective at maintaining security awareness.
Every security incident provides valuable learning opportunities for strengthening future prevention efforts. Document what happened, what worked, what didn’t, and what processes need improvement. Focus this documentation on procedural improvements rather than individual blame—the goal is organizational learning that prevents similar incidents in the future.
EduTranscript – One Platform for All Seven Steps
The obvious question every college registrar asks: “How much time, effort, and resources will implementing these seven security steps actually require?”
We understand the reality. Your team already manages transcript requests, handles verification calls, processes corrections, and deals with compliance audits. Adding 7 separate security implementations sounds like months of disruption, staff training, and budget approvals.
Most institutions struggle with fragmented security solutions that require multiple vendors, complex integrations, and extensive staff retraining. Traditional approaches force registrar teams to coordinate between different software systems, manage multiple user accounts, and reconcile inconsistent data formats. This complexity often leads to security gaps and operational inefficiencies.
EduTranscript eliminates this complexity by integrating all seven fraud prevention methods into a single, unified platform designed specifically for university registrar teams.
Rather than implementing seven different systems and trying to coordinate between them, EduTranscript provides comprehensive transcript security through one integrated solution. This approach eliminates compatibility issues while reducing training complexity and operational overhead.
The platform combines enterprise-grade security with user-friendly interfaces that registrar staff can adopt quickly.
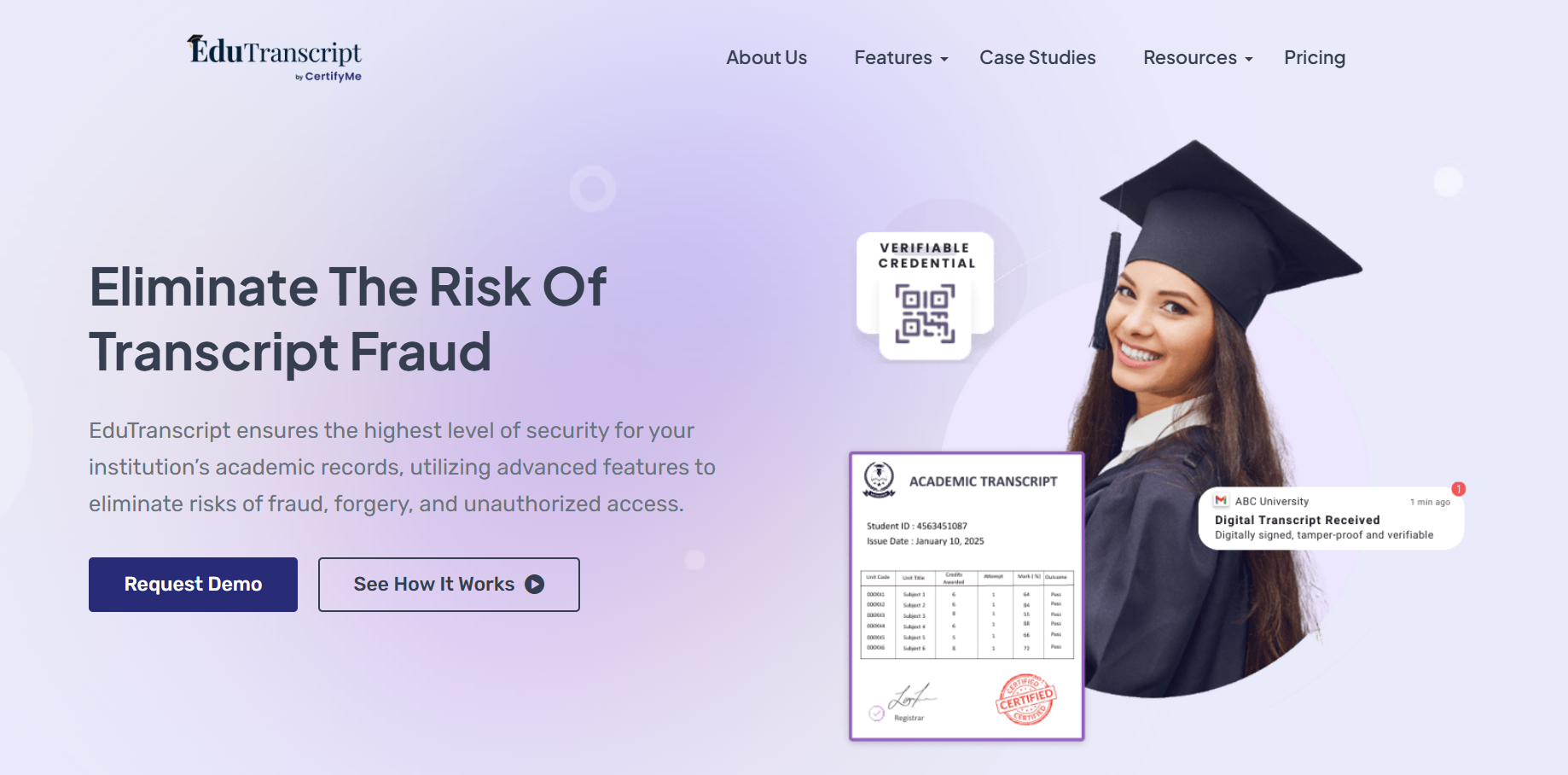
Core Security Features
-
Digital signatures are applied automatically to every issued transcript: The system generates cryptographically secure signatures during the normal PDF creation process. Staff continue using familiar workflows while gaining enterprise-level document security.
-
Decentralized identity management creates unique student identifiers that prevent credential theft: Students receive secure digital identities that link to all their academic records. These identities cannot be transferred, stolen, or duplicated by other individuals.
-
Multi-factor authentication protects both staff accounts and external transcript access: Registrar staff use MFA for system login, while employers and other external parties authenticate through OTP codes sent to students’ verified contact information.
-
Comprehensive audit trails capture every interaction with student records: The system logs all transcript generation, viewing, and verification activities with detailed timestamps and user identification. These logs support compliance audits and forensic investigations.
Operational Benefits
-
Automated verification reduces registrar workload while improving response times: Employers can verify transcript authenticity 24/7 through the built-in verification portal. This eliminates most verification phone calls and emails during business hours.
-
Role-based access controls ensure staff members can only perform appropriate actions: The system enforces permission levels automatically, preventing unauthorized access to sensitive functions like grade editing or bulk transcript generation.
-
Real-time monitoring identifies suspicious activities before fraud occurs: Automated alerts notify administrators about unusual access patterns, failed authentication attempts, and other potential security incidents.
-
Integration with existing student information systems preserves current workflows: EduTranscript connects with Banner, PeopleSoft, and other major SIS platforms through standard APIs. Staff can continue using familiar interfaces while gaining enhanced security.
Implementation Support
-
Dedicated implementation specialists help universities deploy the system quickly: Our team works directly with registrar staff to configure security policies, import existing data, and train users on new procedures. Most institutions complete implementation within 2-4 weeks.
-
Ongoing technical support ensures smooth operations and addresses issues promptly: Universities receive dedicated support resources that understand higher education operations and regulatory requirements. Support includes both technical troubleshooting and policy guidance.
-
Regular system updates incorporate new security features and threat responses: The platform evolves continuously to address emerging fraud techniques and incorporate feedback from registrar users across multiple institutions.
Conclusion
Transcript forgery represents a clear and growing threat to institutional reputation, compliance standing, and public trust.
The sophistication of modern credential fraud demands systematic responses that go beyond traditional security measures. Universities that continue relying on paper documents and manual verification processes expose themselves to significant risks.
Implementing these 7 steps creates layered defenses that make fraud exponentially more difficult and expensive. The investment in comprehensive transcript security might seem cumbersome, but pays dividends through reduced operational overhead, improved compliance standing, and enhanced institutional reputation.
Protecting your students, maintaining employer trust, and safeguarding your institution’s reputation requires action now. Every day of delayed implementation increases exposure to fraud risk. The universities that act decisively will maintain competitive advantages in reputation and operational efficiency.
Are you ready to implement comprehensive transcript security at your institution?
Book a demo with the EduTranscript team to see how these seven fraud prevention steps can be deployed quickly and cost-effectively while actually improving your current transcript management processes.
.png)
 Author :
Author :